One Platform. Limitless Security. By SentinelOne.
A unified, purpose-built platform. With NetDescribe and SentinelOne.
“Autonomous endpoint protection with SentinelOne’s advanced AI powered cybersecurity platform.”
Ilker Duman | SentinelOne Expert at NetDescribe

The Challenge
Too many products, too many alerts, too few people.
Organisations try to protect their data by deploying more and more endpoint agents. It is not unusual to find six to eight security agents running on the same device. Existing tools generate a constant stream of alerts — but how are you supposed to identify and prioritise the ones that truly matter? Skilled IT staff and security experts are in high demand, yet increasingly difficult to find.

SentinelOne – the Solution from NetDescribe
The SentinelOne Endpoint Protection Platform unifies prevention, detection and response in a single, purpose built agent powered by machine learning and automation. It provides prevention and detection of attacks across all major vectors, rapid threat elimination through fully automated and policy guided response actions, and complete visibility across the endpoint environment with full context and real time forensics.
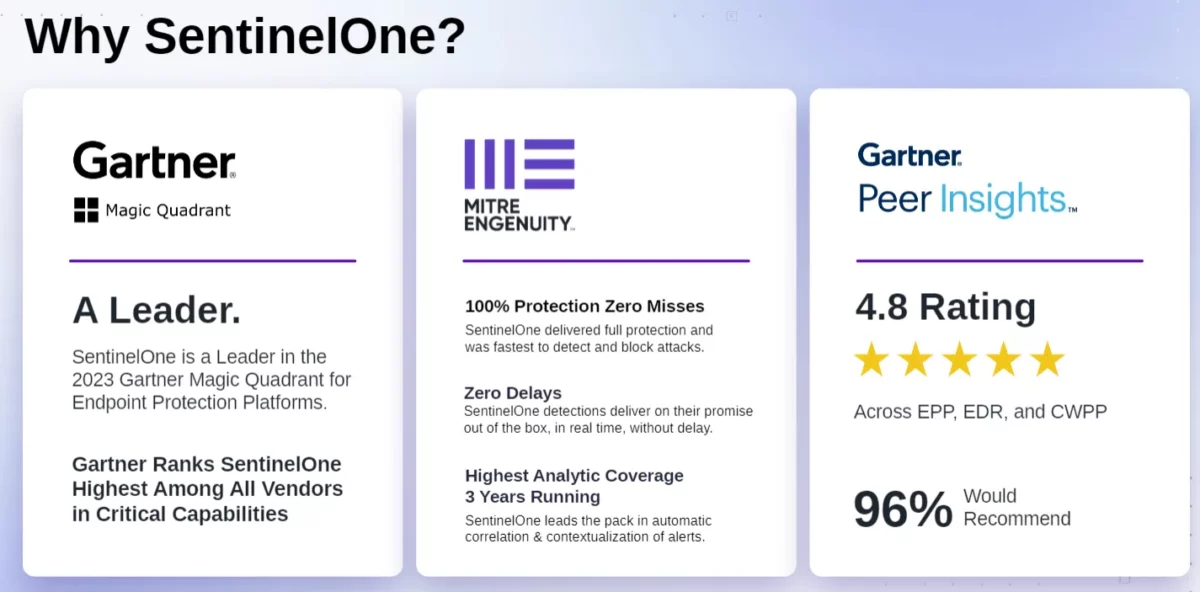
The challenge for all companies
Too many isolated tools
Security teams are forced to manually investigate and respond to alerts across multiple tools.
Severe shortage of qualified personnel
This results in reduced security and a significantly higher likelihood of security incidents.
Digital transformation
Limited visibility and insufficient protection dramatically increase the attack surface.
Source: www.sentinelone.com
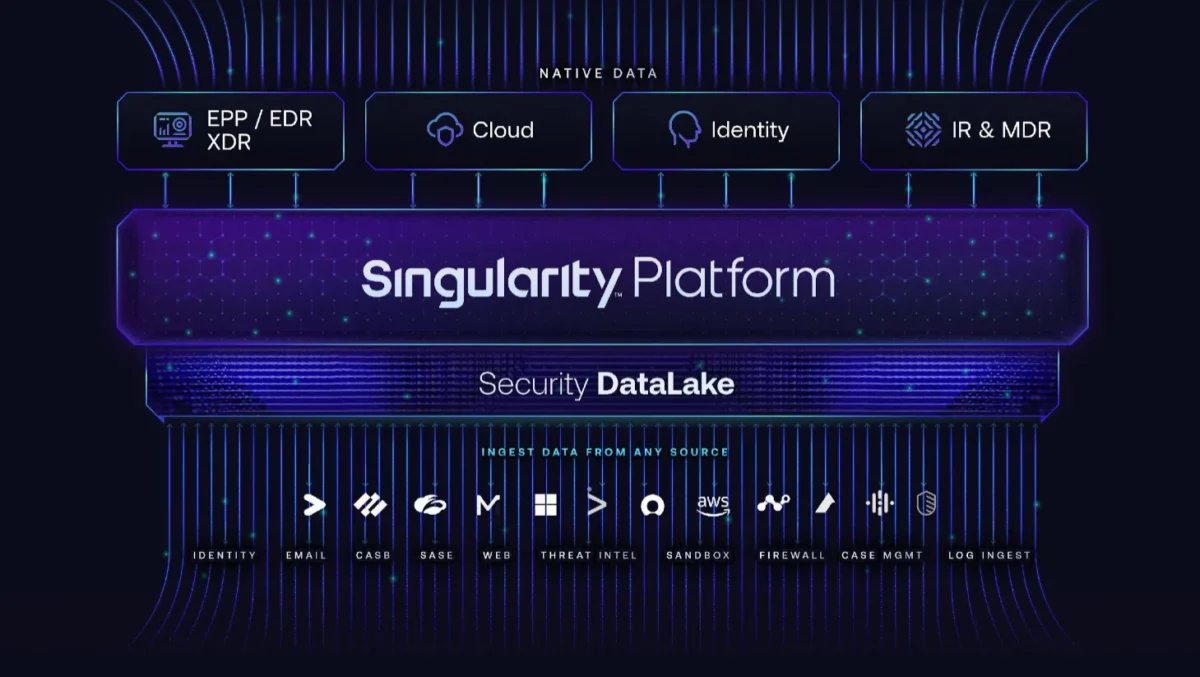
The value of the Singularity Platform
A single console and platform – Consolidate vendors and train employees on one solution.
Open ecosystem of best of breed tools – Increase the return on investment of your existing tools.
Ease of Use – Employees only need to be trained on a single solution.
Unprecedented protection – MITRE Leader with 100% prevention.
Superior automation – Streamlined SOC workflows.
Unified Data Lake – The only security solution built on a single, unified data platform for security and operations.
Time to value – Full deployment and protection across the entire organisation within days.
Lower TCO – Consolidate multiple agents and vendors. Data retention costs are only a fraction of current usage.
Source: www.sentinelone.com
SentinelOne Products
Singularity Endpoint
Industry-leading EPP/EDR
Fastest MTTR with highest accuracy. Freeing up resources for investigations that truly matter.
Optimised security
A central management console, improved security posture and increased SOC efficiency through automation.
Increased analyst efficiency
Reduced alert fatigue and a lower manual triage burden for SOC teams, enhanced by the added value of integrated ITSecOps tools.
Singularity XDR
Increase the ROI of existing tools
Open ecosystem with bidirectional response measures.
Reduction of TCO
Consolidate vendors and agents, reduce training needs and free analyst time through automation.
Unified Security Data Lake
The only platform built on a single unified data store, enabling advanced security analytics and insights.
Singularity Identity
Secure Active Directory
Protect identity stores, identify and remediate risky vulnerabilities and security gaps.
Identity Threat Detection & Response
Prevent identity based attacks, credential theft, reconnaissance and lateral movement.
Deceive attackers
Deploy decoys that attract attackers and provide meaningful insight into their behaviour.
Singularity Cloud
Workload resilience & integrity
Detection of attacks with machine speed in real time. Automated recovery. No kernel panic.
Forensic visibility
Accelerate IR, simplify threat hunting. Ephemeral Workload Flight Data RecorderTM.
Digital transformation
Accelerate innovation with runtime security that stays out of the way. No kernel dependencies. Fully aligned with DevOps deployment methods.
Incident Response & Managed Detection & Response
SOC efficiency & adaptability
Maintain confidence that your environment is under control, even as new threats emerge, with all in one MDR and active campaign threat hunting.
Insight & actionability
Reduce day to day workload and receive only the insights you need, when you need them, so you can focus on strategic initiatives
Incident Response
Seamlessly dive deeper into suspicious activities or call the integrated MDR and DFIR team from Vigilance, as well as the extensive partner network, for hands on support.
SentinelOne’s Purple AI
SentinelOne’s Purple AI is an advanced generative AI assistant for cybersecurity, built to simplify and accelerate security operations. It enables analysts to run complex threat hunts and investigations using natural language queries that are automatically translated into precise searches across both native and third party data. Purple AI sorts alerts, summarises results and creates collaborative investigation notebooks, dramatically reducing detection and response times — often by up to 80 percent. With the release of Athena, it gained “agentic AI” capabilities that enable autonomous reasoning, the creation of detection rules and the execution of remediation across any SIEM or data source. Designed with strong privacy safeguards and transparent operations, Purple AI helps organisations respond to threats faster, improve SOC efficiency and scale expertise across teams.
The features and benefits that SentinelOne’s Purple AI offers:
- Natural language interface: Lowers the barriers to threat hunting and investigation.
- Automatic triage and summaries: Accelerates threat response with best practices aligned to MITRE.
- Investigation notebooks: Improve transparency, collaboration and knowledge sharing.
- Agentic AI (Athena): Automates end to end workflows, from detection through to response.
- Data-independent integration: Works with a wide range of SIEMs and data sources.
- Data protection and transparency: Designed for accountability and privacy.
Read the full IDC report to discover how AI is transforming cybersecurity across industries: https://www.sentinelone.com/lp/idc-business-value-purple-report/
SentinelOne Use Cases – Read our specific Customer Stories
Our UseCases are only available in German. If you are interested in further information, we are happy to assist you personally. Please do not hesitate to contact us directly.
Endpoint Detection & Response with SentinelOne
Our customer from the automotive supplier industry asked NetDescribe to replace a legacy antivirus solution and ensure continuous 24/7 monitoring. IT specialists have been working on endpoint security for decades. In most cases, the signature of new malicious code is detected by common antivirus products, and the respective vendors roll out updated rules to protect their customers.
In this scenario, however, IT teams are the ones constantly being hunted. They have to identify new attacker techniques in order to protect themselves — around the clock. But what about the malicious programs that no one has seen before, the so-called zero days? Read more in our Use Case: Endpoint Detection & Response with SentinelOne
NetDescribe SentinelOne Paladin Experts

Downloads and Links
Book your personal consultation now
Put your IT performance to the test now. What requirement have you always been looking for a solution for? NetDescribe will get you to your goal – through independent advice, reliable support and proven use cases.
Blog
Interesting Facts from the IT World
-

Combined Splunk expertise within the Xantaro Group: greater transparency, security, and efficiency for our customers
NetDescribe and anykey are pooling their Splunk expertise within the Xantaro Group. Customers benefit from greater transparency, security, and efficient observability and SIEM solutions from…
-
NetDescribe Use Case – Visibility with Splunk IT Service Intelligence
Splunk IT Service Intelligence (ITSI) provides a comprehensive view of the status of your IT services—from infrastructure to business processes. KPI monitoring, machine learning, and…
-

Xantaro Group integrates specialists for technically sophisticated IT infrastructure solutions anykey GmbH
anykey GmbH, an IT system house founded in 1999 and based in Troisdorf, is now part of the Xantaro Group. With this step, the two…