Armis Centrix™ the Cyber Exposure Management Platform by Armis
Identify and classify ALL devices in your infrastructure. With NetDescribe and Armis Centrix™.
“Close gaps, secure your assets, and manage your cyber risks.”
Stefan Stettin | Armis Specialist at NetDescribe

The Challenge
The rapid increase in the number of managed and unmanaged OT/IoT devices in the work environment, coupled with expanding cloud deployments and the shift toward remote work, presents a major challenge for IT and security experts. Inadequate or missing security capabilities in laptops, smartphones, smart TVs, webcams, printers, HVAC systems, and industrial control systems complicate their detection and management. To identify all devices across their networks, manage risks effectively and secure their environments, companies need a reliable solution. That’s exactly what you can achieve with Armis Centrix.

Armis – the Solution from NetDescribe
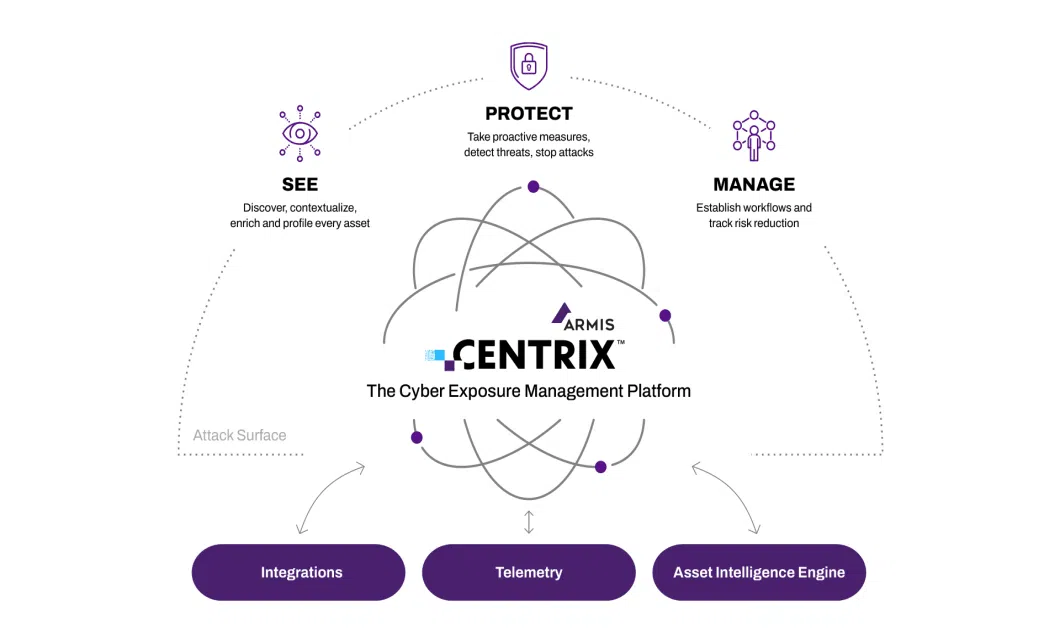
Armis Centrix™ enables companies to see, protect, and manage all physical and virtual assets, so that the entire attack surface can be defended and managed in real time. Focus on what’s essential: See everything, recognize real risks, proactively mitigate threats.
Source: www.armis.com
Armis Device Knowledge Base
Armis Centrix™ is a cloud-native, AI-driven platform for cyber risk management that proactively secures all assets, addresses vulnerabilities, blocks threats, and protects the entire attack surface. By providing full visibility and context for every asset in the enterprise environment, Armis Centrix™ enables organizations to establish a strong and effective line of defense. The goal is to prioritize the use of resources according to the relevance of the risks. Risk assessments, policies, alerts, and visualizations are used for this purpose.
Armis Centrix™ can also be seamlessly integrated with existing enforcement and ticketing tools to ensure continuous workflows and establish an effective risk lifecycle management process. This allows organizations to track their progress in reducing risks and proactively take action, detect threats, and stop attacks.
Armis Platform
Armis Centrix™
Armis Centrix™, is a comprehensive platform for managing cyber risks driven by an advanced AI-powered Asset Intelligence Engine that recognizes, secures, protects, and manages billions of assets around the world in real time. The cloud-native, frictionless platform proactively mitigates all cyber asset hazards, remediates vulnerabilities, blocks threats, and protects your entire attack surface.
Armis Centrix™ for Asset Management and Security
Benefit from a powerful and efficient approach to asset management:
- Maintain full visibility into your inventory at all times.
- Quickly identify and eliminate gaps and optimize the security of your IT network.
- Define policies to enforce security controls on your devices and ensure regulatory and industry compliance.
- Gain actionable cyber insights to detect and combat threats in real time across the entire attack surface of your assets.
Armis Centrix™ for OT/IoT Security
Protection and security of critical infrastructures 24/7:
- Understand the risks of Operational Technology (OT).
- Detect, secure, protect, and manage every OT device – including SCADA, PLC, and DCS – as well as the supporting resources that keep operations running.
The coverage of Armis Centrix™ spans your entire environment – from the factory floor to the executive suite. This matters because attackers see your environment as one large, interconnected cyber attack surface.
Armis Centrix™ for Medical Device Security
Continuous security, optimized utilization: Armis Centrix™ identifies and protects IoMT, IoT, OT, and IT assets that are essential for connected care.
Optimize your security posture and manage the complex medical devices that define modern healthcare.
Take the next step in securing managed and unmanaged devices without interruption, and protect both your assets and the people who depend on them.
Armis Centrix™ for Vulnerability Prioritization and Remediation
Focus on the CVEs (Common Vulnerabilities and Exposures) that matter!
Armis Centrix™ assigns each asset a contextual risk score based on its business criticality, the severity of its vulnerabilities, and its exploitability. This information enables you to focus your resources where they are needed the most.
Armis Centrix™ for Actionalble Threat Intelligence
Anticipate attacks and stop them before they strike: Transform your security strategy by identifying and blocking threats before they impact your business!
Armis Centrix™ for Actionable Threat Intelligence combines advanced AI and machine learning technologies and serves as an early warning system that enables you to neutralize threats by:
- Anticipating attacks
- Understanding their potential impact
- Taking preventive action
This allows you to effectively switch from defense to offense!
Armis Centrix™ for Actionable Threat Intelligence offers a revolutionary AI technology that leverages the dark web, dynamic honeypots, and HUMINT to promptly stop attacks.
Armis Managed Threat Services
Gain a decisive edge and stay protected: In today’s dynamic digital age, aligning security measures with business objectives is of utmost importance. Discover how Armis Managed Threat Services seamlessly close this gap and turn potential cybersecurity challenges into opportunities for stronger protection and growth.
Accelerate your journey toward continuous, business-driven cyber resilience.
Armis Managed Threat Services (MTS) enable SOCs and Security Operations teams to harness centralized, contextual asset intelligence across the entire technology stack to optimize operations within your evolving business and threat landscape.
Armis Features
Detect
Attack Surface Visibility – Armis Centrix™ provides the ability to detect all physical and virtual assets – locally and in the cloud – ensuring complete visibility and real-time defense and management of your entire attack surface.
Unified Asset Inventory
Armis Centrix™ seamlessly integrates with your existing IT and security tools and aggregates, deduplicates, and normalizes data for every asset in your environment. It provides agentless, non-intrusive monitoring. This is critical because many devices simply cannot tolerate a traditional security agent, and scans can disrupt or crash sensitive environments. This gives you a single source of truth with a complete, accurate, and real-time inventory that helps you streamline your operations.
Asset Intelligence, Context, and Behavior
The AI-powered Asset Intelligence Engine adds contextual information to each asset, enabling your IT and security teams to prioritize remediation based on threats, risks, and criticality. This gives you the ability to make informed decisions and take action where it matters most.
Detection of Vulnerabilities, Risks, and Threats
The cloud-based Armis Centrix™ Threat Detection Engine uses machine learning and artificial intelligence to detect when a device is operating outside of its normal “known good” baseline. Its network detection and analytics features enable security teams to make informed, data-driven decisions to prioritize security measures based on the data collected from the network by Armis Centrix™.
Protect
Companies must take proactive steps to detect threats and stop attacks. Armis Centrix™ ensures that the entire attack surface is continuously defended in real time.
- Define policies and integrate them with existing enforcement tools
Trigger policy-based actions at your Network Enforcement Points to automatically block, quarantine, or isolate risky or malicious devices. If Armis Centrix™ detects that a device is behaving abnormally, it can instruct your network firewall to block communication with the Internet, effectively stopping a threat before it develops into a full-scale attack.
Prioritize the risks and vulnerabilities most relevant to your business
Armis Centrix™ calculates its comprehensive risk score based on several factors, including issues such as unpatched software versions, known hardware exploits, and vulnerabilities. This risk score helps your security team take preventive actions to reduce the attack surface and supports you in complying with regulatory requirements that require the identification and prioritization of all vulnerabilities.
Enrichment of SOC, SIEM, and SOAR
Accelerate incident response and investigation by having asset and security information available in one place. Armis Centrix™ integrates effortlessly with SIEM and other security solutions to deliver the context-rich intelligence needed to strengthen your security posture without disrupting current operations or workflows.
Manage
Attack Surface Management: Armis Centrix™ provides the ability to build a comprehensive cybersecurity program by managing your company’s cyber risks in real time. It integrates with your existing workflows and makes it easy to track and report progress.
Integration with existing tools to enable end-to-end workflows and enforce security policies
Workflow integration with security and orchestration solutions enables automated responses to detected risks. The reaction can be as simple as
- opening a ticket in JIRA and notifying the responsible team,
- quarantining the compromised device through your Network Enforcement Tools until it is fixed and verified, or even
- performing fully automated remediation or patching of the compromised asset.
Continuous assessment of compliance with internal and external policies
Armis Centrix™ helps you meet your internal compliance requirements and prepare for external audits. Whether it’s NIST, CIS Controls, GDPR, NIS2, or other regulations, Armis helps you ensure that your security standards are met while minimizing human error in data collection.
Track and Report Risk Reduction Over Time
Continuously review how your existing security controls (EDR, vulnerability scanners, etc.) and identify gaps in implementation. Armis Centrix™ finds all assets that are not protected and helps to quickly fix the problems. Stay informed in real time, effortlessly track progress, and improve your security posture.
Armis Performance Features
COMPREHENSIVE: Detection and classification of all devices
AGENTLESS: No installation and configuration on devices, no disruption to ongoing operations
PASSIVE: No impact on your corporate network, no active scanning
SEAMLESS: Installation within minutes in your existing infrastructure
Risk Assessment
The Armis Engine continuously monitors the behavior of every device in your LAN and WLAN for anomalies. Using an extensive knowledge base, Armis Centrix™ compares real-time behavior against the following criteria:
- historical device behavior
- behavior of comparable devices in your environment
- behavior of comparable devices in other environments
- known attack techniques
- information from threat intelligence feeds
Based on this data, Armis Centrix™ identifies threats and attacks.
Detection and Response
When a threat is detected, Armis Centrix™ can alert security teams and automatically take action to prevent an attack. By integrating with switches, WLAN controllers, and existing security devices, such as Cisco and Palo Alto Networks firewalls, as well as network access control (NAC) solutions, like Cisco ISE and Aruba ClearPass, Armis Centrix™ can restrict access or quarantine suspicious or malicious devices. This automation ensures that an attack on any device – whether managed or unmanaged – is stopped, even when your security team is focused on other priorities.
Seamless Integration
Armis Centrix™ requires no agents or additional hardware for deployment and is therefore ready for use in no time. It can be integrated not only into your firewall or NAC solution, but also into security management systems such as SIEM, Incident Response, and ticketing systems. This allows your security team to use these systems to leverage the valuable insights that Armis Centrix™ provides.
Armis Data Sources
Armis Asset Intelligence Engine
Armis’ collective, AI-driven Asset Intelligence Engine monitors billions of assets worldwide to uncover patterns and indicators of cyber risk. It powers Armis Centrix™ with real-time, actionable intelligence to detect, understand, and neutralize threats across the entire attack surface.
Telemetry Intelligence
Armis Centrix™ collects, correlates, and analyzes massive volumes of telemetry data to uncover deep insights and empower more informed, data-driven decisions.
Integrations
With hundreds of seamless, API-based integrations, Armis Centrix™ maximizes the value of your existing security investments by correlating data from a wide range of tools — including endpoint protection, vulnerability scanners, SaaS applications, inventory solutions like CMDB systems, and more.
Armis Centrix™ Smart Active Querying
Secure and proactive discovery of assets combined with data enrichment for IT, OT, IoT, and IoMT devices.
Armis Business Benefits – Asset Management at it’s best
Transparency is the foundation of any corporate security strategy. To meet compliance requirements, organizations must maintain a complete, up-to-date record of all hardware and software assets.
Armis Centrix™ automatically identifies and classifies every device — managed or unmanaged, IoT or OT — within your environment. This includes servers, laptops, smartphones, VoIP phones, smart TVs, IP cameras, printers, HVAC controllers, medical devices, and industrial control systems.
Armis Centrix™ can even identify devices operating outside the network via WLAN, Bluetooth, and other IoT protocols – all without requiring additional hardware.
The comprehensive asset inventory generated by Armis Centrix™ contains important data such as device manufacturer, model, serial number, location, username, operating system, installed applications, and connections made. Beyond detection and classification, Armis Centrix™ evaluates each asset’s risk profile using multiple factors, including known vulnerabilities, attack patterns, and behavioral anomalies within your network.
Based on these insights, your security team can pinpoint critical weaknesses, prioritize mitigation efforts, and ensure compliance with regulations requiring vulnerability identification and prioritization.
Watch the Video
Downloads and Links
Book your personal consultation now
Put your IT performance to the test now. What requirement have you always been looking for a solution for? NetDescribe will get you to your goal – through independent advice, reliable support and proven use cases.
Blog
Interesting Facts from the IT World
-

Combined Splunk expertise within the Xantaro Group: greater transparency, security, and efficiency for our customers
NetDescribe and anykey are pooling their Splunk expertise within the Xantaro Group. Customers benefit from greater transparency, security, and efficient observability and SIEM solutions from…
-
NetDescribe Use Case – Visibility with Splunk IT Service Intelligence
Splunk IT Service Intelligence (ITSI) provides a comprehensive view of the status of your IT services—from infrastructure to business processes. KPI monitoring, machine learning, and…
-

Xantaro Group integrates specialists for technically sophisticated IT infrastructure solutions anykey GmbH
anykey GmbH, an IT system house founded in 1999 and based in Troisdorf, is now part of the Xantaro Group. With this step, the two…