Cloud Computing, Security and Content Delivery (CND) by Akamai
Benefit from unmatched transparency and proactively adapt your security strategy. With NetDescribe and Akamai.
“Save time, reduce expenses, and minimize security risks through host-based segmentation!”
Joseph Kolb | Akamai Guardicore Segmentation Expert at NetDescribe

The Challenge
IT landscapes are becoming increasingly heterogeneous and dynamic — workloads are growing exponentially. Comprehensive insights and deep visibility regarding network activities and threats are becoming a decisive success factor. Continuous review and validation of users and devices are essential for IT security. The challenge lies in delivering a powerful combination of security, performance, scalability, and transparency that helps companies protect their digital assets and achieve their business goals.

Akamai – the Solution from NetDescribe
The Akamai Connected Cloud platform offers companies several advantages:
- Security optimization: The platform effectively protects web applications and APIs from persistent cyber threats, which is crucial for safeguarding brand reputation. Akamai uses advanced security mechanisms to ward off attacks and ensure the integrity of data and services.
- Zero Trust model: By implementing the zero-trust model, Akamai offers comprehensive coverage and deep visibility. This means that every element in the network is considered potentially insecure until it is verified, which raises security to a new level.
- Optimized user experience: Akamai improves the user experience by optimizing applications and APIs. Fast loading times and reliable performance ensure that users are satisfied and happy to return.
In summary, the Akamai Connected Cloud platform offers a robust solution for security, visibility, and performance optimization that helps companies stay competitive in an increasingly digital and threatened environment.
Akamai Cloud Computing
Reduce costs, improve performance, and shorten time to market.
With the world’s broadest cloud platform, you can deliver applications and workloads close to your end users, no matter where they are.
Download: Cloud Computing Overview
Download: Product-Brief Cloud Computing
Akamai Solutions for Application and API Security
API Security

Source: www.akamai.com
API Security gives you comprehensive insights into your entire API environment through continuous discovery and real-time analysis. Discover all APIs, including shadow APIs, identify common vulnerabilities, and analyze API behavior to uncover threats and logic abuse in this rapidly growing attack vector.
Read more: API Security
App & API Protector
App & API Protector combines Web Application Firewall, Bot Defense, API Security, and DDoS protection in a single solution, including Layer 7 DDoS protection. This solution quickly detects vulnerabilities and stops threats in the most complex web and API architectures. App & API Protector is the leading solution for attack protection on the market. It is easy to implement and use and offers automatic security updates as well as a comprehensive view of traffic and attacks.
+++ Stop evolving attacks with smarter security +++
Most WAFs struggle to keep up with evolving threats, leaving applications and APIs vulnerable to zero-day attacks, API abuse, and sophisticated DDoS or bot-based fraud attempts. Many security teams have to manually update rules, optimize policies, and add third-party tools for protection. This slows down response times and increases false positives.
Akamai Adaptive Security Engine provides automated real-time protection for edge, cloud, and hybrid environments. The solution continuously updates security policies based on global threat intelligence and protects against OWASP Top 10 threats, CVEs, and API exploits. App & API Protector Hybrid extends WAF protection beyond the CDN and secures North-South and East-West traffic for a unified security posture.
Download: Product-Brief App & API Protector
Client-Side Protection & Compliance
Client-Side Protection & Compliance prevents the theft of end-user data and protects websites from malicious JavaScript activity. It monitors script behavior in real time, provides actionable insights in a central dashboard view, and issues alerts to prevent malicious script activity. Designed for PCI DSS v4.0, it helps organizations meet new security requirements for web-based scripts and protect themselves from client-side attacks.
Akamai Products for Zero-Trust Security
Akamai Guardicore Segmentation
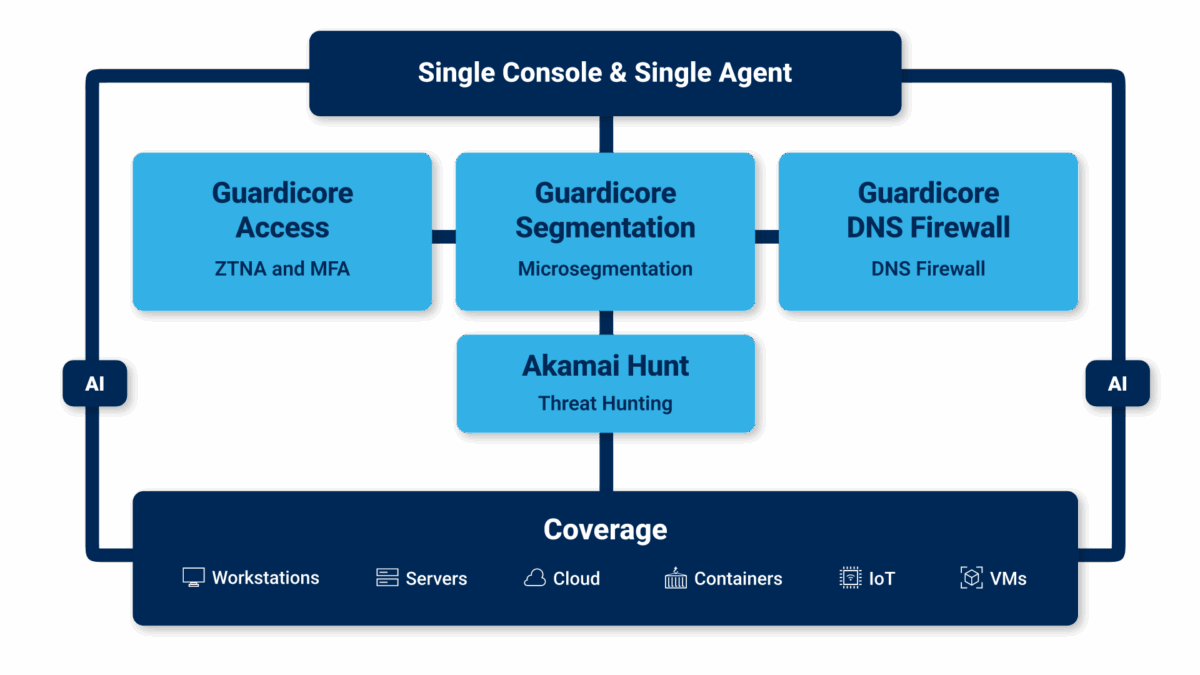
The Akamai Guardicore Platform combines microsegmentation, Zero Trust Network Access, MFA, DNS firewall, threat hunting, and AI to provide zero-trust security.
Source: www.akamai.com
For many companies, implementing zero trust security is a major challenge. The requirements are complex and the investment is not insignificant. The protective measures cover all assets on-site and in the cloud, as well as all workplaces, including remote work.
Learn more about the Akamai Guardicore Platform here: Your Path to Zero Trust
One of the core components of the Akamai Guardicore Platform is microsegmentation.
Akamai Guardicore’s host-based network segmentation is revolutionizing the market for traditional firewalls. The software-only approach is decoupled from the physical network and offers a faster alternative. Akamai Guardicore Segmentation is designed for agile companies and offers more security and visibility in the cloud, data center, and endpoint. The key features are:
Broad coverage – Microsegmentation policies are implemented wherever your applications run – in public, private, or hybrid cloud environments.
Deep Visibility – Akamai’s solution helps you understand the full context through application discovery and mapping of dependencies before you define security policies.
Intuitive Workflow – Akamai Guardicore Segmentation offers a simple workflow. From mapping application dependencies to recommending and defining rules. This allows you to understand relationships in order to optimally apply them to data traffic.
Granular policies – Now you can define and enforce rules at the process level. This allows you to precisely control the flow between individual application components in order to achieve the highest level of security.
High flexibility at low cost – Akamai’s solution is more cost-effective, efficient, and adaptable than traditional firewalls.
Microsegmentation provides a detailed view of network traffic. This gives administrators better control over the data. In addition, microsegmentation can be used to identify data traffic that requires preferential treatment or management. This can include data that needs to be specially protected to comply with regulations or standards.
Finally, microsegmentation is a core component of sophisticated security concepts, such as zero-trust networking. This is used to verify the identity of a user before they can access a device on the network.
Dividing data center and cloud environments into individual logical parts makes it possible to protect critical data, processes, and systems against attacks. This involves enforcing the highest security policies, monitoring data flows between data centers, and isolating data access.
Download: Product-Brief Akamai Guardicore Segmentation
You want to learn more: Akamai Guradicore Segmentation
Secure Internet Access
Secure Internet Access Enterprise is a cloud-based DNS firewall that empowers security teams to ensure that all users and devices – both inside and outside the network – can securely access the internet. It proactively blocks malicious DNS requests, including malware, ransomware, phishing, and low-throughput DNS data exfiltration. Secure Internet Access reduces security complexity by eliminating the need to deploy, manage, and update hardware. It is also easy and intuitive to use.
Download: Product-Brief Secure Internet Access
Hunt
Akamai Hunt is a managed threat hunting service that uncovers and eliminates hidden security risks in your environment. Led by security experts from Akamai’s threat intelligence and analysis teams, Akamai Hunt uses data from the Akamai Guardicore Segmentation solution to track down threats in your network, identify and virtually remediate vulnerabilities, and protect your infrastructure.
Download: Product-Brief Hunt
Enterprise Application Access
Akamai Enterprise Application Access is a Zero Trust Network Access solution that enables precise access to private applications based on identity and context. It uses identity-based policies and real-time data such as user location, time, and device security to ensure that users can only access the applications they actually need, without requiring network-level access. The solution works seamlessly with Akamai MFA to ensure strong user authentication.
Download: Product-Brief Enterprise Application Access
Akamai MFA
Akamai MFA protects your employees’ logins for cloud, web, on-premise, SaaS, and IaaS applications through the FIDO2 authentication standard. The solution offers a user-friendly mobile push notification and eliminates the need for expensive hardware security keys. Akamai MFA integrates seamlessly with Akamai Enterprise Application Access, supporting a comprehensive Zero Trust Network Access (ZTNA) solution.
Download: Product-Brief MFA
Akamai and Linode – The Revolution of Cloud Usage for Developers
Akamai Blog – Why this merger makes so much sense: https://www.akamai.com/de/blog/news/linode-akamai-transform-how-developers-use-the-cloud
Provisioning Kubernetes clusters with the Akamai Container Orchestration Module.
The Linode Kubernetes Engine is a fully managed K8s container orchestration service for deploying and managing containerized applications and workloads. LKE combines ease of use and simple pricing with infrastructure efficiency.
This way, you can have your infrastructure and workloads up and running in minutes instead of days. Get to know the Linode Kubernetes Engine (LKE): https://www.linode.com/de/products/kubernetes/
Akamai Use Cases – Explore our Customer Stories
Our UseCases are only available in German. If you are interested in further information, we would be happy to assist you personally. Please don’t hesitate to contact us directly.
Akamai Guardicore – Network Segmentation in the Textile Industry
Cyber attacks on retail companies have increased sharply over the last 12 months. Attackers typically target business-critical IT assets, that, if compromised, bring the entire operation to a standstill. When intruders are successful, ransom payments are often demanded as the next step. This is known as a ransomware attack. Our customers had already experienced security incidents and were looking for a way to reduce attack surfaces and safeguard critical resources from ransomware. They wanted a simple, fast, and scalable solution that complements their existing IT infrastructure without requiring costly security hardware.
Read more in our Use Case Network Segmentation in the Textile Industry
Akamai Guardicore – Network Segmentation for Distributed Locations
The number of successful cyber attacks on German companies is growing. Attackers are no longer limiting themselves to local resources, but are expanding their attacks to the entire IT landscape. The increasing interconnectedness between devices, tools and users works in their favor. Many companies lack the necessary security practices to consistently protect their environments and data across multiple data centers and clouds. This has led businesses to ask whether cyber insurance from major providers is enough to reduce the risk of an attack — and how to meet the insurers’ requirements for obtaining it.
Read more in our Use Case Network Segmentation for Distributed Locations
Downloads and Links
Book your personal consultation now
Put your IT performance to the test now. What requirement have you always been looking for a solution for? NetDescribe will get you to your goal – through independent advice, reliable support and proven use cases.
Blog
Interesting Facts from the IT World
-

Combined Splunk expertise within the Xantaro Group: greater transparency, security, and efficiency for our customers
NetDescribe and anykey are pooling their Splunk expertise within the Xantaro Group. Customers benefit from greater transparency, security, and efficient observability and SIEM solutions from…
-
NetDescribe Use Case – Visibility with Splunk IT Service Intelligence
Splunk IT Service Intelligence (ITSI) provides a comprehensive view of the status of your IT services—from infrastructure to business processes. KPI monitoring, machine learning, and…
-

Xantaro Group integrates specialists for technically sophisticated IT infrastructure solutions anykey GmbH
anykey GmbH, an IT system house founded in 1999 and based in Troisdorf, is now part of the Xantaro Group. With this step, the two…