Next-Gen Network Detection & Response by Exeon
With Exeon.NDR, you benefit from a leading network security solution that helps you meet legal compliance requirements. With NetDescribe and Exeon Analytics.
“Protect your IT/OT infrastructure through immediate detection of potential cyber threats and rapid, efficient responses.”
Mikhail Elchin | Exeon Analytics Expert at NetDescribe

The Challenge
Cyber incidents such as ransomware attacks, data breaches, and IT disruptions, as well as the associated risks of business interruptions in a dynamic IT/OT landscape, are putting companies on high alert.
Distributed and hybrid networks are difficult to analyse and monitor. Added to this are new compliance regulations such as the NIS2 directive and the Digital Operational Resilience Act (DORA), which hold management accountable in cases of insufficient IT security measures. Selecting the right security solutions, conducting thorough risk assessments and ensuring continuous training are essential.

Exeon Analytics – the Solution from NetDescribe
Exeon.NDR, the leading network security solution, uses machine learning to deliver comprehensive network monitoring, immediate detection of potential cyber threats and rapid, efficient response to protect your organisation.
As a reliable and intuitive software solution, Exeon.NDR not only supports your security teams in their day to day work but also elevates your network security to the next level.
How does an AI-powered solution work?
The algorithms behind Exeon.NDR generate a unified view from metadata, allowing organisations to continuously analyse and monitor their IT, cloud and OT networks through a single application. This prevents attackers from moving unnoticed between environments, exploiting vulnerabilities, infiltrating infrastructure or bypassing existing security controls.
How Exeon.NDR works:
Exeon.NDR analyses security relevant log data from networks and systems. As a pure software solution, it uses the existing company infrastructure — such as firewalls, switches and other components — as data sensors, requiring no additional hardware appliances or dedicated sensors.
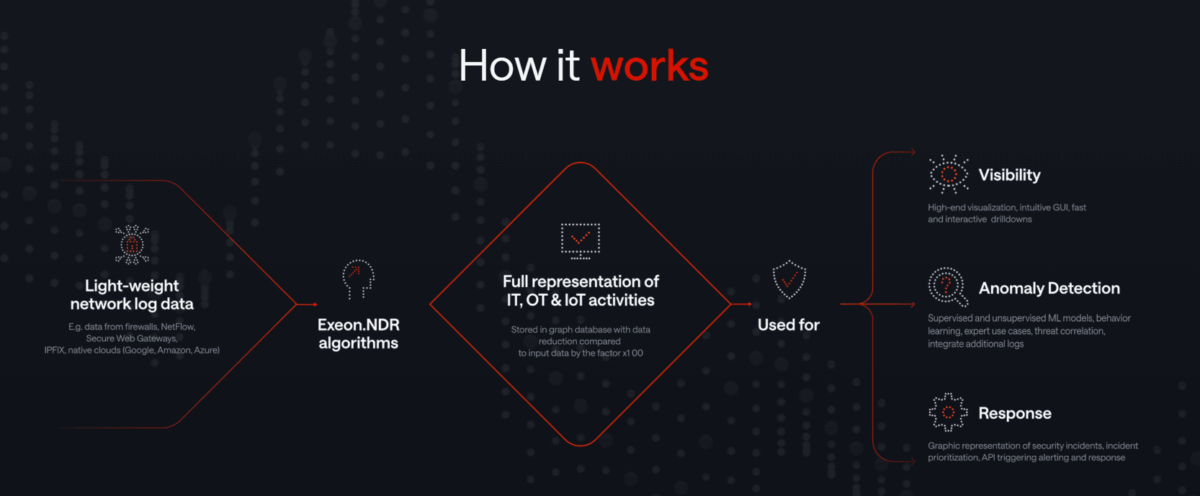
Source: www.exeon.com
The most advanced NDR (Network Detection and Response)
Exeon.NDR’s future ready approach is based on metadata analysis and therefore does not require traffic mirroring. Its AI algorithms are specifically designed to analyse encrypted data that conventional Network Detection and Response solutions cannot process. Exeon.NDR also enables the analysis of multiple data sources, including native cloud applications, making it the leading solution for highly virtualised and distributed networks.
Why Exeon does not rely on traffic mirroring: Most network traffic today is already encrypted. Conventional NDR solutions that depend on traffic mirroring are unable to inspect large portions of this traffic. In addition, increasing bandwidths make traffic mirroring either extremely expensive or practically impossible. In contrast, Exeon.NDR collects metadata simply by exporting logs from the existing infrastructure.
The collected metadata is translated into observable actions within the network. These actions are then grouped into traces, each representing a sequence of activities that can be linked to a specific user. Every attacker leaves such a trace behind, with no way to avoid it. These traces are analysed by the machine learning model to identify potentially malicious behaviour.
Compliance and Zero Trust
The goal of every company is to strengthen security while meeting legal requirements – ideally achieving both at once.
Exeon.NDR makes exactly this possible by connecting Zero Trust principles with compliance and cybersecurity regulations, along with other key security standards.
To improve compliance with regulations such as NIS2, HIPAA, and GDPR, it is essential to understand their specific requirements and determine the necessary data protection measures, access controls, and security safeguards. Zero Trust strategies such as implementing microsegmentation, adhering to the principle of least privilege, and using encryption for data transmission and storage are indispensable.
Network Detection and Response (NDR) plays a vital role in aligning a Zero Trust strategy with compliance mandates. NDR strengthens cybersecurity and helps companies meet regulatory demands. By continuously monitoring and analyzing network traffic, NDR identifies anomalies and potential threats, offering deep visibility and enabling timely incident response.
Discover how NetDescribe and Exeon can help elevate your security strategy to the next level.
Exeon.NDR – The Platform

With the modular design of Exeon.NDR, you can tailor the advanced NDR solution precisely to your needs. The platform serves as the central intelligence of Exeon.NDR, driving all modules and correlating network events from across your data sources.
Correlation Engine
Cross-data source algorithms to combine and correlate relevant security data from all available systems to provide you with a unified, complete picture for transparency, detection, assessment, investigation and remediation.
SecurityDB
Graph database for efficient storage of enriched security data, requiring up to 50x less volume than log data. Supports high scalability and long-term event history retention.
Alerting System
Exeon.NDR’s alerting functionality, plus a REST API for forwarding alerts to systems such as ticketing platforms, SIEM, SOC tools or SOAR.
Incident Handling
User interface for processing incidents directly within Exeon.NDR.
Incident Assessment
Algorithms for automatic assessment and prioritisation of detected security incidents, minimising false alarms and helping teams focus on the right issues.
Dashboard & Reporting
Customisable dashboards, incident evaluation and reporting, and an intuitive interface for operating Exeon.NDR.
Visualizations
Dedicated, intuitive visualisations tailored to specific data sources and threat scenarios. Provides optimised views for incident investigation and guided threat hunting.
AI based Detection-Analysis
Ready-made AI-driven analysis algorithms and use cases designed for specific data sources and their respective threat scenarios.
Data Lake (Option)
If you already use a data lake in Splunk or Elasticsearch, Exeon.NDR integrates with it seamlessly. If not, Exeon.NDR offers its own powerful and cost-effective data lake.
Exeon.NDR – The Modules
The modules provide specialized AI capabilities for collecting, processing, analysing and visualising data, as well as for detecting and investigating threats within specific data sources. Powerful software collectors handle log data efficiently, eliminating the need for additional hardware or software sensors.

The modules make your network more secure and smarter – whether used together or individually:
Network Module: Monitoring of internal & external network traffic for NetFlow, IPFIX, Corelight & DNS
- Detection of ATP attacks
- Network transparency
- Analysis of access patterns for internal services
- Identification of internal shadow IT
- Blacklist matching
Web Module: Monitoring of the web activities of internal devices (proxy/secure web gateway) for proxy logs from SSL/TLS-monitoring Secure Web Gateways
- Detection of ATP attacks
- Discovery of hidden data leaks
- Identification of external shadow IT
- Detection of unauthorised or outdated devices
- Identification
- Blacklist matching
Xlog Module: Cross-source threat detection for additional security-relevant log data
- Better events – Enriched, aggregated and correlated across multiple data sources, stored efficiently
- Better Detection – Correlation and enrichment of network events with host log data
- Better Alerts – Combining host- and network-based alerts to filter false positives and produce consolidated, high-quality notifications
- Better Response
Exeon.NDR – On Prem or On Cloud
Cloud-based cybersecurity offers cost efficiency through a consumption-based model and scalable resources without significant upfront investment. Cloud providers handle maintenance, updates and security patches, while also enabling remote monitoring and management. On-premises solutions require higher upfront costs and ongoing maintenance, but they provide maximum customisation, full control over infrastructure and data, and lower latency for real-time threat detection. They are more resilient to physical disasters and offer stronger data protection for organisations with strict privacy requirements.
Cloud risks include potential Trojan infections, insufficient encryption, dependence on Internet connectivity and complex regulatory compliance. Companies in regulated industries often prefer on-premises solutions due to complete data control, better performance, higher reliability and greater flexibility.
Exeon.NDR is a flexible Network Detection and Response (NDR) platform that can be deployed both in the cloud and on premises. It analyses network metadata, requires no costly mirroring or decryption, and is simple to deploy and maintain. Exeon.NDR adapts seamlessly to specific organisational requirements.
Exeon.NDR – Business Benefits
Fast Setup
Operational within hours, with no sensors or agents required.
Comprehensive Visibility
United view of distributed NW, endpoints and applications.
Full IT/OT Network Monitoring
Identify malicious attack patterns and vulnerabilities in real time, including impaired services, shadow IT and more.
Unaffected by Encryption
Algorithms remain effective even when data is encrypted, as detection relies on metadata analysis rather than deep packet inspection.
Lightweight Data Processing
Analysis of lightweight network protocol data instead of traffic mirroring. Metadata can be streamed from existing network sources (switches, firewalls, etc.) without hardware sensors.
Smart Detection
Powered by advanced AI and proven detection algorithms.
Intelligent Data Handling
Minimal storage requirements while maintaining full data sovereignty – whether deployed on premises or in the cloud.
Powerful Response
Rapid assessment, investigation and remediation.
Future-Proof
Ready for increasing data volumes and rising levels of encryption.
Book your personal consultation now
Put your IT performance to the test now. What requirement have you always been looking for a solution for? NetDescribe will get you to your goal – through independent advice, reliable support and proven use cases.
Blog
Interesting Facts from the IT World
-

Combined Splunk expertise within the Xantaro Group: greater transparency, security, and efficiency for our customers
NetDescribe and anykey are pooling their Splunk expertise within the Xantaro Group. Customers benefit from greater transparency, security, and efficient observability and SIEM solutions from…
-
NetDescribe Use Case – Visibility with Splunk IT Service Intelligence
Splunk IT Service Intelligence (ITSI) provides a comprehensive view of the status of your IT services—from infrastructure to business processes. KPI monitoring, machine learning, and…
-

Xantaro Group integrates specialists for technically sophisticated IT infrastructure solutions anykey GmbH
anykey GmbH, an IT system house founded in 1999 and based in Troisdorf, is now part of the Xantaro Group. With this step, the two…