Our Use Case PDFs and blog images are only available in German. If you are interested in further information, we are happy to assist you personally. Please don’t hesitate to contact us directly.
Get the PDF for download here: Cyber Security | KRITIS Requirements Trading Company
1. The Initial Situation
Our client is subject to the KRITIS regulation in the food sector and must ensure that the required level of cyber security and IT security is implemented for the KRITIS systems.
Perimeter firewall monitoring was identified as one of the most important action points. The element manager system for managing the firewalls did not offer a sufficiently long retention and analysis option for log events.
How Can the KRITIS Requirements of the BSIG be Implemented in My Company?*
The BSI-Kritis regulation obliges operators of critical infrastructures, among other things, to take appropriate precautions to avoid disruptions […] of their information technology systems, components and processes” according to the “state of the art” and to prove this to the BSI.
“State of the art” is a common legal term. Technical development is faster than legislation. It has therefore proven its worth in many areas of law for years to refer to the “state of the art” in laws instead of trying to define specific technical requirements in the law. What is the “state of the art” at a certain point in time can be determined, for example, on the basis of existing national or international standards and norms from DIN, ISO, DKE or ISO/IEC or on the basis of successfully tested models for the respective area.
*Source: www.bsi.bund.de
The implementation of these legal requirements poses enormous challenges for the companies concerned and, above all, for the teams involved in the design. It’s easy to lose track.
The First Step towards Legal Certainty and Clarity: Visibility of the Availability of all your IT Services!
What is often lacking is data-driven insights for comprehensive visibility and rapid detection of attacks and other threats in your IT landscape.
At the top of the companies’ wish list:
- end-to-end transparency in all your environments,
- fast threat detection,
- efficient investigations,
- an open and scalable system that can be integrated into your structures and
- analyses available at any time according to your individual requirements.

2. The Use Case
The group of companies from the retail sector with a sales area in southwestern Germany – across Baden-Württemberg, Rhineland-Palatinate and Saarland as well as parts of Hesse and Bavaria – employs around 47,000 people, including the colleagues in independent retail, including around 3,000 trainees.
In 2022, they achieved a consolidated external turnover of 10.3 billion euros. This puts them in one of the top positions in the national retail network.
The company’s goal was to meet the necessary requirements for a KRITIS audit, as well as to implement modern security standards to protect against failures and threats.
The NetDescribe Solution – Splunk Enterprise Security
The use of Splunk Enterprise Security enables companies to consistently monitor, evaluate, and visualize distributed data centrally via log analysis, thus providing valuable insights from the machine data.
Correlation rules and reports can be created to immediately identify irregularities and threats and automatically detect areas with violations.
3. The Approach
In a proof of concept, the possibilities of Splunk were evaluated together with the customer in relation to their requirements. During this phase, the configuration of the Splunk environment was already aligned in such a way that a later seamless transfer to the production environment was possible.
For the analysis of the log events for typical security-relevant behavior and anomalies, a distributed Splunk environment with two indexers, a manager node and a search head was established.
The analysis platform provided was dimensioned to retain the required log data for one year. In contrast to the manufacturer’s management system, this enabled the customer to retain the log file 10 times longer and make it available for analysis.
Splunk Enterprise Security
Splunk Enterprise shows the availability of your IT services from a real user perspective. Both the distribution of problems of any kind and the rapid identification of their causes.
Splunk Enterprise grows with your requirements and is infinitely scalable. It is possible to solve individual problems, as well as holistic, strategic monitoring scenarios, e.g. for Application Delivery, IT Operations, Security & Compliance & Fraud, Business Analytics, IoT & Industrial Data.
4. The Implementation
The first presentation of the possible solution was carried out for the customer in February 2019 as part of an operational intelligence demo, in which the Splunk experts from NetDescribe were able to convince with the technical possibilities of Splunk Enterprise.
At the beginning of March 2019, a PoC was planned in which dedicated use cases and corresponding success criteria were agreed together with the customer.
In April 2019, a Splunk infrastructure was set up in the data center directly at the customer’s site, which was already designed during the PoC phase in such a way that the system could go into productive operation after a successful test.
On May 27, 2019, the customer ordered 100GB of Splunk Enterprise for one year and consulting for the final implementation of the solution, as well as the connection of the planned data sources and the evaluation within the framework of dashboards and reports.
Despite massive restructuring in the company and an associated change of contact person, the customer extended for another year. At this point it was already foreseeable that another branch would also be connected to Splunk in the future. New management, new use cases and data sources (Windows and Linux server logs) and more intensive use of Splunk then led to a doubling of the license a year later.
In May 2022, the customer had recognized the strategic value of Splunk for his company and extended it for another 24 months, combined with an order for 500GB of Splunk Enterprise.
Thanks to the continuous and targeted advice of the NetDescribe consultants, the company decided to intensively expand the use of Splunk, so that a further doubling of the volume is planned for the next upcoming extension.
After a successful PoC of Splunk Enterprise Security, the SIEM solution from Splunk was also budgeted and will be implemented in the next financial year.
Splunk SIEM (Security Information and Event Management)
- Full transparency in all your environments
- Faster threat detection and investigation
- More flexibility and compatibility of different tools and technologies
Splunk Architecture*

Use Cases for Splunk PoC:
- Integration of the decentralized Checkpoint Firewall
- Checkpoint App
- Integration of the Sandblast systems
- Integration of the 2 Perimeter FW’s Firepower
- Suggestions for Security Monitoring Use Cases
- Infosec App
- Splunk Security Essentials App
MITRE ATT&CK*

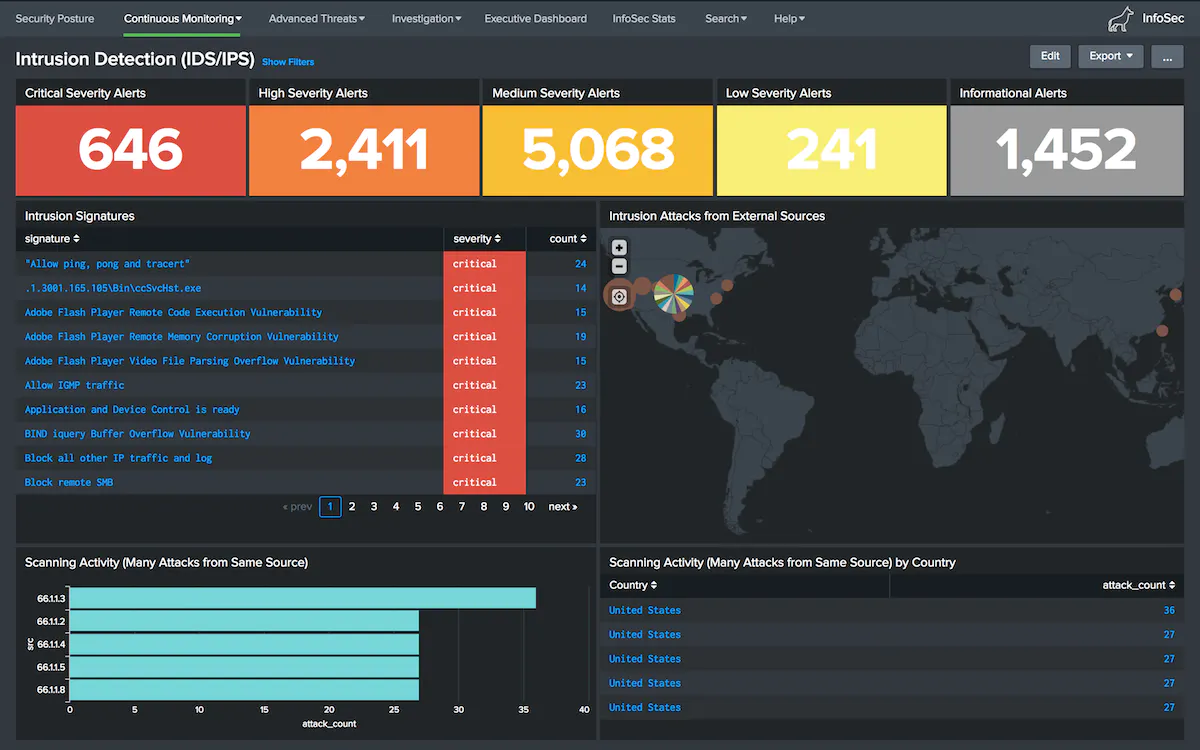
Intrusion Detection*
Incident Review*
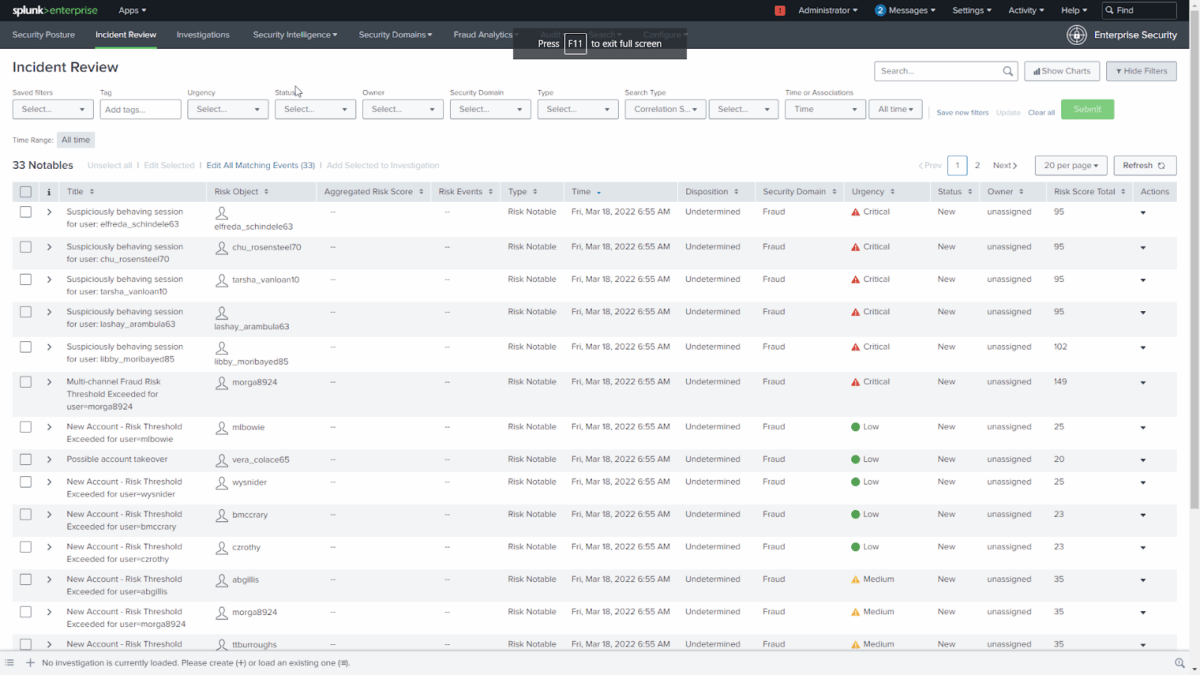
*Source: Splunk
5. The Results
- A strong security architecture means fewer security breaches for your company. The fast and comprehensive implementation of the solution ensures that the KRITIS requirements with regard to auditing and compliance are continuously met and the risks for our customer have been drastically reduced.
- Analyses and reports are always available, no matter when and in what form they are needed – e.g. convincing functions for evaluating the firewall logs of our customer.
- Restructuring and redesigning business processes – a topic for many companies. With Splunk Enterprise Security and NetDescribe’s targeted approach, a trusting cooperation was always guaranteed, despite changing contact persons. This was the only way the successful implementation and operation were possible.
- Cost savings and resource conservation through business continuity and protection of critical infrastructures and data.
- Customer satisfaction and increased confidence in the company through transparency and continuous language and responsiveness.
- Through the piloting of Enterprise Security as a SIEM tool for the developing SOC, our customer can reach the next stage of his Security Maturity journey.
The Splunk Portfolio
Splunk platform.
Splunk Enterprise collects and indexes in real time all machine data generated in physical, virtual, or cloud environments. This can include data from applications, servers, networks, sensors, or telecommunications equipment. The solution correlates complex events, enables meaningful insights into machine data and simplifies analyses.
Splunk for security.
Splunk Enterprise Security improves all security processes and, as an analysis-driven SIEM (Security Information and Event Management) solution, gives you the holistic view to securely use generated machine data (e.g. information about networks, endpoints, accesses, vulnerabilities and identity data) and to reduce security breaches.
Splunk for IT and Business Services.
Splunk IT Service Intelligence (ITSI), as a monitoring and analysis solution, visualizes status data and key performance indicators (KPIs) of critical IT and business services. Splunk ITSI uses machine-driven (artificial) intelligence, identifies existing and potential problems, prioritizes the rapid recovery of business-critical services, and provides analytically driven IT operations.
The Splunk Functions at a Glance
Collection and indexing of machine data – Real-time event capture, universal indexing, adapter elimination, use of metric data, timestamps for events
Search and verification – Real-time search, transaction search, interactive results
Correlation and analysis – Machine-learning-based AI, correlation of complex events, event annotations, pattern recognition
Visualization and reporting – Dashboard creation, report automation
Monitoring and alerting – Monitoring of events and KPIs, proactive notifications
Security and administration – Encrypted access to data streams, secure user access
Get the PDF for download here: Cyber Security | KRITIS Requirements Trading Company