Our Use Case PDFs and blog images are only available in German. If you are interested in further information, we are happy to assist you personally. Please don’t hesitate to contact us directly.
Download the PDF here: From Logging to Managed Security Operations Center
1. The Initial Situation
Our client – a full-service provider in the field of internal rating procedures for corporate customer business – has been using Splunk Enterprise since 2019 to collect and evaluate log data from its own applications.
However, collecting data and using standard dashboards often only utilizes a fraction of the potential of this data.
The definition of individual dashboards adapted to customer needs in order to generate relevant insights from the collected data involves various challenges that can be of both a technical and organizational nature. The raw data must be transformed, filtered and aggregated accordingly in order to generate meaningful metrics.
This already starts with data integration. Data often comes from different sources that have different formats, structures and update intervals. Choosing the right structure is crucial for performance and scalability. Large amounts of data require efficient queries and caching strategies to avoid performance problems. Too many metrics or poor arrangement of elements can make readability and interpretation difficult. Filters, drilldowns and dynamic visualizations must be integrated in a meaningful way.
This requires a targeted and trusting cooperation with the customer in order to understand, interpret and effectively implement the requirements.

2. Requirements analysis
At the end of 2023, we agreed with our client’s CISO to implement Splunk and Splunk Enterprise Security as a SIEM in the company. The integration should take place in the customer’s existing systems, which are primarily operated on-premise.
There should also be corresponding monitoring with 24/7 alerting, which would reach its second expansion stage with a Managed SOC.
Together with our customer and our Managed Security Team, we developed a concept to implement Splunk and Splunk Enterprise Security with Cribl as a “data hub” in the customer’s data center.
It quickly became clear that very close coordination and collaboration were required to leverage the potential of the chosen solution.
Because even the most beautiful dashboard is only useful if it is actually actively used by users. Training and feedback loops are important. Dashboards must be updated regularly and adapted to new requirements.
And this is where NetDescribe GmbH comes into play. We support the specialist departments within the framework of consulting and technical workshops, with the aim of generating ever better analyses, dashboards and reports and thus guaranteeing our customers the best possible benefit from their software products in combination with their data and processes.
3. The Use Case
Our client provides comprehensive support to banks and financial institutions in the development, implementation, maintenance and optimization of internal rating systems. These rating systems are used to assess the creditworthiness of major customers (e.g. companies, institutional investors). Through these services, a full-service provider ensures that banks can use efficient, regulatory-compliant and competitive rating procedures in the corporate customer business.
The customer’s core business is ensuring data integrity and availability, which makes a SOC – and even better a Managed SOC – essential to protect data, comply with regulatory requirements and detect cyber attacks at an early stage. Since such companies work with critical financial information, a SOC is a central component of the IT security strategy for
- Protecting sensitive financial and customer data,
- Compliance with regulatory requirements (GDPR, DORA, BaFin…),
- Defending against cyber attacks on critical infrastructures,
- Securing the IT infrastructure and cloud environments and
- Avoiding financial damage and loss of reputation.
The Solution from NetDescribe
Implementation of Splunk and Splunk Enterprise Security as SIEM in the company. 24/7 monitoring and continuous optimization with our consultants in the Managed Security Service.
4. The Implementation
Thanks to the many years of experience of our consultants, the project to set up the SIEM was implemented in the planned time and without any problems. After the implementation, the operation of the SIEM was gradually taken over and the planned use cases were operated by our team as a Managed Security Service and continuously further developed.
There are currently around 100 active use cases, including:
- Detection of brute-force attacks through correlation and analysis of authentication attempts
- Geolocation-based anomaly detection of logins from unauthorized or unknown regions
- Detection of unexpected driver changes to identify potential persistence mechanisms or manipulations
- Process monitoring using Sysmon, including anomalies in process starts, parent-child relationships, and unusual behavior
- Monitoring of privileged and high-risk user accounts, such as Office 365 Risky Users or local administrators, for early identification of compromised identities
Managed SOC – the solution for missing in-house resources
As in many companies, our customer lacked the technical resources and the necessary know-how to develop and build up the project with their own specialists. Here, external resources as part of outsourcing to NetDescribe offer an important addition and open up the possibility of operational support by our consultants.
SIEM setup
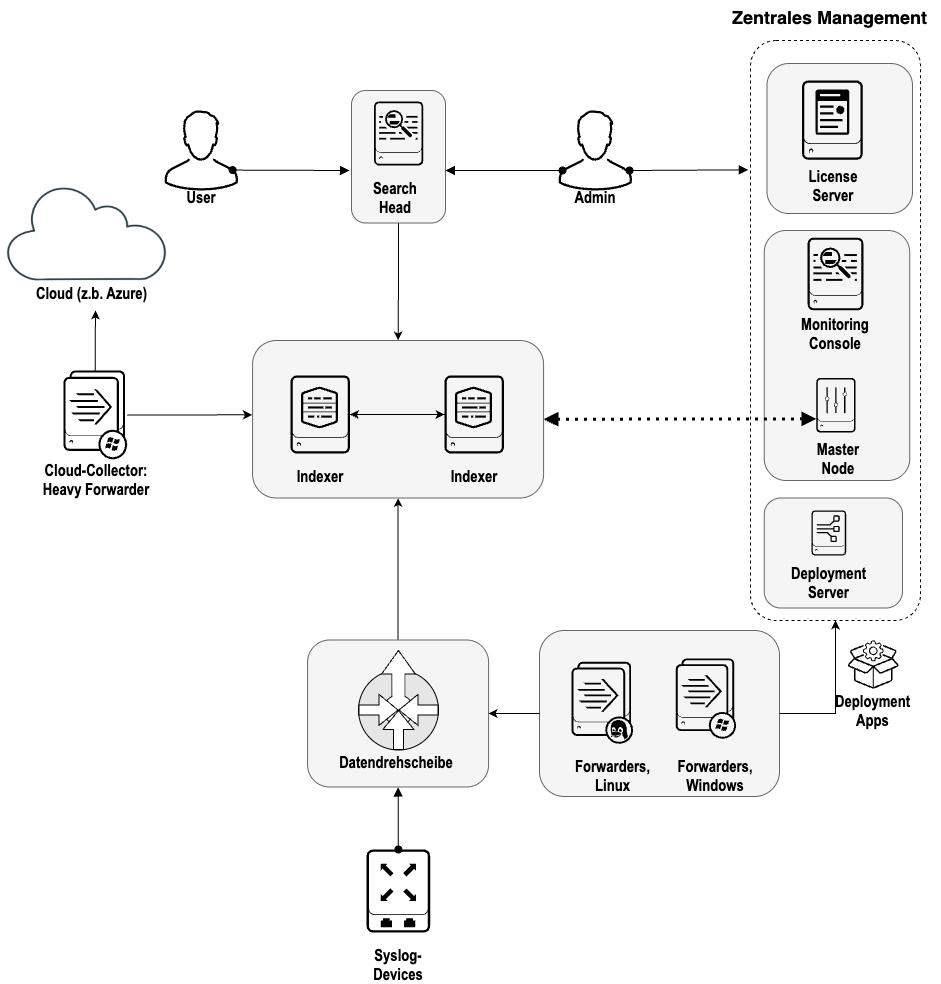
The “data hub” offers you an Observability Pipeline that gives you the flexibility to collect, reduce, enrich, normalize and forward data from any source to any destination within your existing data infrastructure.
Excerpt from the dashboard*

MITRE Mapping*

MITRE Mapping refers to the assignment of security-relevant findings, threats or attack techniques to the MITRE ATT&CK frameworks. A cyber threat, attack or security incident is mapped to specific tactics and techniques within the MITRE ATT&CK matrix.
Read also our NetDescribe Security TAKE AWAY #3 – MITRE ATT&CK Matrix
Why is MITRE Mapping important?
- Detection of attacks: Security events and threats can be matched with MITRE ATT&CK techniques to understand which attack paths were used.
- Incident Response: Teams can take action faster if an attack has been assigned to a specific MITRE tactic.
- Threat modeling: Security strategies can be improved by analyzing past attack patterns and comparing them with MITRE techniques.
- Automation & SIEM/SOAR integration: Many security platforms (e.g. SIEMs, EDRs) use MITRE Mapping to automatically link events with ATT&CK techniques.
*Source: Splunk
5. The Results
- Since our Managed Security Service Team continuously monitors the alarms for our customers and drives the analysis of incidents, we relieve the customer’s operations team.
- Our customer has the opportunity to continuously adapt its use cases to current requirements and thus draw the optimal insights from the collected data.
- Optimal use of resources through NetDescribe Managed Services: With the external services, the customer purchases IT resources and expert knowledge without having to train their own employees for a long time and withdraw them from other important projects.
- Security at the highest level: Small and medium-sized companies in particular benefit from the concentrated know-how within the Managed Security Service Team. Many years of expertise of our SOC analysts ensures the protection of your sensitive data and the maintenance of a strong cybersecurity structure.
- Our Managed SOC increases security, reduces risks and ensures compliance. In particular, companies that operate in the area of critical infrastructures or work with them benefit from a Managed SOC, as it protects sensitive data and meets strict regulatory requirements.
The Splunk Portfolio
Splunk platform. Splunk Enterprise collects and indexes in real time all machine data generated in physical, virtual, or cloud environments. This can include data from applications, servers, networks, sensors, or telecommunications equipment. The solution correlates complex events, enables meaningful insights into machine data and simplifies analyses.
Splunk for security. Splunk Enterprise Security improves all security processes and, as an analysis-driven SIEM (Security Information and Event Management) solution, gives you the holistic view to securely use generated machine data (e.g. information about networks, endpoints, accesses, vulnerabilities and identity data) and to reduce security breaches.
Splunk for IT and Business Services. Splunk IT Service Intelligence (ITSI), as a monitoring and analysis solution, visualizes status data and key performance indicators (KPIs) of critical IT and business services. Splunk ITSI uses machine-driven (artificial) intelligence, identifies existing and potential problems, prioritizes the rapid recovery of business-critical services, and provides analytically driven IT operations.
The Splunk Functions at a Glance
Collection and indexing of machine data Real-time event capture, universal indexing, adapter elimination, use of metric data, timestamps for events
Search and verification Real-time search, transaction search, interactive results
Correlation and analysis Machine learning-based AI, correlation of complex events, event annotations, pattern recognition
Visualization and reporting Dashboard creation, report automation
Monitoring and alerting Monitoring of events and KPIs, proactive notifications
Security and administration Encrypted access to data streams, secure user access
Download the PDF here: From Logging to Managed Security Operations Center