Our Use Case PDFs and blog images are only available in German. If you are interested in further information, we are happy to assist you personally. Please don’t hesitate to contact us directly.
Get the PDF for download here: SIEM | Entertainment and E-Commerce with Splunk Enterprise Security
1. The Initial Situation
The customer had reached the limits of the existing SIEM (Security Information and Event Management) platform Logrythm. The long-term security goals could no longer be achieved. This concerned, for example
- new log formats that were not supported,
- variable log formats that required greater dynamism,
- but also technical scaling and stability problems.
How can the fail-safe operation of the systems be maximized?
With an optimized SIEM, the fail-safe operation of your systems can be maximized. A simple, standardized extension of the monitoring/SIEM function, rapid integration of complex environments, as well as interfaces and dashboards “out of the box” ensure higher quality, more flexibility and efficiency, as well as a significant cost reduction.
The key to this: automation and visualization of data analysis!
Although the amount of machine data is increasing, a uniform database is lacking for analysis and evaluation. The goal is to centralize, correlate, and analyze the data throughout the IT network in order to identify security problems and react in real time.

2. The Use Case
The media company is one of the leading entertainment and e-commerce providers in German-speaking countries. The entertainment portfolio is complemented by digital consumer brands in the Commerce & Ventures and Dating & Video segments.
The company’s goal was to increase IT security by detecting threats, complying with regulatory requirements, and generally improving incident management in IT security.
The NetDescribe Solution – Splunk Enterprise Security
The use of Splunk Enterprise Security enables companies to consistently monitor, evaluate, and visualize distributed data centrally via log analysis, thus providing valuable insights from the machine data.
Correlation rules and reports can be created to immediately identify irregularities and threats and automatically detect areas with violations.
3. The Implementation
The first demo of the Enterprise Security solution on site at the customer’s premises with the help of “Splunk SHOW/ House of Demos” was very successful and questions could be answered comprehensively.
The next step was to define a Proof of Concept that should include the most important sources as well as the implementation of some use cases that could not be mapped in the previous solution.
This POC phase took place in the context of workshops in order to impart as much know-how as possible right from the start. This enabled the customer to implement use cases independently very quickly.
After the order was placed, the project plan was created. The installation of Splunk Enterprise and Splunk Enterprise Security took place in the customer’s data center.
After the order was placed, the project plan was created. The installation of Splunk Enterprise and Splunk Enterprise Security took place in the customer’s data center.
You can see the architecture here:
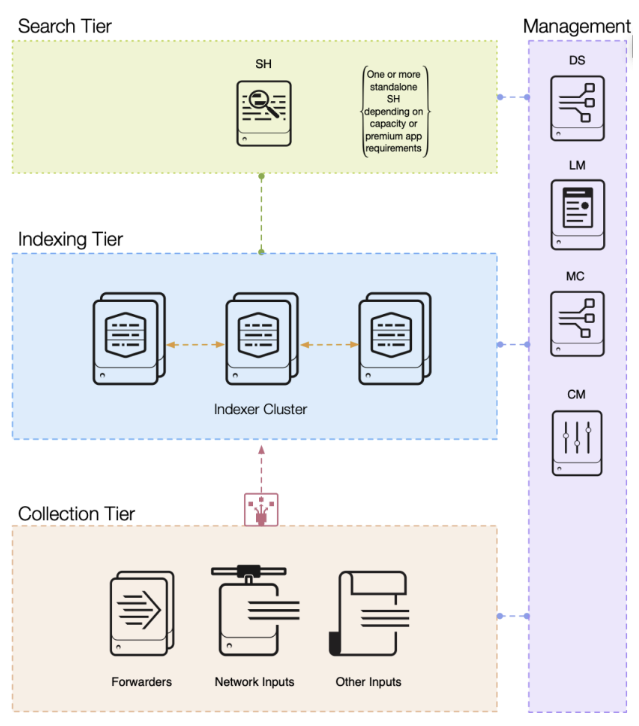
Source: Splunk
- Splunk Enterprise Security was set up as a distributed environment
- Index cluster with local storage (1 year retention)
- 4-digit number of Universal Forwarders, managed via the deployment server
- 2 Searchheads (Adhoc + Splunk Enterprise Security)
- Integration of Splunk configs with versioning software (GIT)
- Sketchy architecture
Kinesis AWS Infrastructure:

The following data sources were connected:
- Endpoint Security / several anti-virus solutions in use
- Virtualization infrastructure
- Custom applications
- Cloud – Azure and AWS (with AWS Firehose / ELB / Lambda)
- Server OS Logs
- Proxy Logs
- Loadbalancer Logs
- ERP System
4. The Results
- Due to the many years of experience of NetDescribe’s employees, the tight schedule could be met.
- Even after the project was accepted, continuous support was provided as part of an operational support service. New data sources were added and further security use cases were implemented.
- Data sources that could not be connected to the previous solution due to format-related technicalities were successfully connected to Splunk Enterprise Security in a very short time (0.5-2 days per source).
- Data sources that required extra licenses in the previous solution did not require any additional licenses in Splunk Enterprise Security.
- All sources were normalized in Splunk Enterprise Security. This is a crucial aid in use case creation, as everything is Splunk CIM compliant.
What the customer says about working with NetDescribe:
“The collegial, efficient, and careful working methods of the NetDescribe team enabled us to set up our complete SIEM infrastructure in just three months and carry out a seamless hotswap from LogRythm to Splunk.”
The setup was not just a duplication of our old environment, but also an improvement with new network zone concepts to ensure the security of our log data.
Splunk Enterprise – Business Benefits
Splunk Enterprise shows the availability of your IT services from a real user perspective. Both the distribution of occurring problems of any kind and the rapid identification of their causes.
Splunk Enterprise grows with your requirements and is infinitely scalable. Possible are the solution of individual problems as well as holistic, strategic monitoring scenarios, for example for Application Delivery, IT Operations, Security Compliance & Fraud, Business Analytics, IoT & Industrial Data.
The Splunk Functions at a Glance
Collection and indexing of machine data – Real-time event capture, universal indexing, adapter elimination, use of metric data, timestamps for events
Search and verification – Real-time search, transaction search, interactive results
Correlation and analysis – Machine-learning-based AI, correlation of complex events, event annotations, pattern recognition
Visualization and reporting – Dashboard creation, report automation
Monitoring and alerting – Monitoring of events and KPIs, proactive notifications
Security and administration – Encrypted access to data streams, secure user access
Get the PDF for download here: SIEM | Entertainment and E-Commerce with Splunk Enterprise Security