Our Use Case PDFs and blog images are only available in German. If you are interested in further information, we are happy to assist you personally. Please don’t hesitate to contact us directly.
1. The Initial Situation
Cyber Attacks on Retail Companies
…have increased sharply in the last 12 months.
The attackers usually focus on business-critical IT assets, the failure of which can bring the entire operation to a standstill. If the intruders are successful, the next step is to demand ransom payments. This is known as a ransomware attack.
What is “Ransomware”?
Ransomware, also known as extortion Trojans, extortion software, crypto Trojans or encryption Trojans, is a form of digital extortion.
Specifically, it is malicious software that cybercriminals use to prevent access to company data or IT systems and demand a ransom.
Ransomware blocks basic computer functions and/or encrypts critical operating and user data. The affected companies are threatened with destruction or publication of the data until they pay the ransom. The goal is always to disrupt or completely shut down normal operations.
In the case of the retail sector, the attackers usually target the POS systems or the server landscape of the companies.

2. The Use Case
The Requirement for NetDescribe
In this specific case, it involved two companies from the textile trade with several hundred branches in the DACH region. Both companies had already struggled with security incidents and were looking for a solution to reduce attack surfaces and protect critical resources from ransomware. In short, a simple, fast and scalable solution that complements the existing IT infrastructure without requiring costly security hardware.
The Performance Solution from NetDescribe
After an analysis of the current situation, a segmentation of the network with the technology of Guardicore (Akamai) was recommended in addition to the existing security measures.
What is Guardicore (Part of Akamai)?
The Guardicore Centra platform is a software-based solution for network segmentation. It enables comprehensive transparency at the process level, behavior-based policies and real-time detection of security breaches to protect your company’s most important resources. As a result, you get a cost-efficient, fast solution for consistent security – no matter the application, no matter the IT environment.
What is Network Segmentation?
Network segmentation involves dividing your network into small, separate segments (subnetworks). Often, the network is divided into three logical zones: “Trusted Zone, DMZ & Management Zone”,
in order to be able to isolate them from each other with security controls.
It is important that all systems within a zone have similar protection requirements. The yardstick and pacemaker here is the system that places the highest demands.
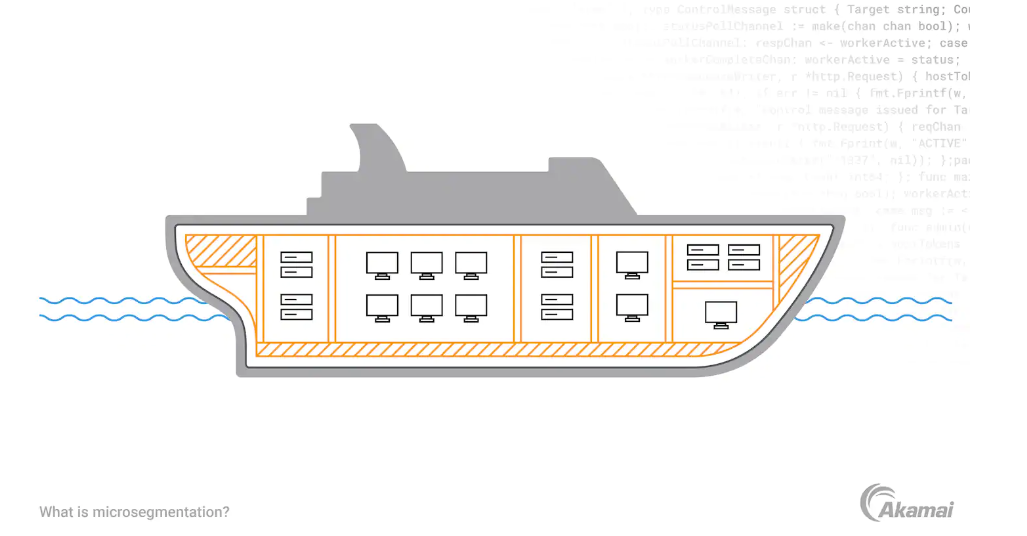
What Does Microsegmentation Mean?
The most effective method of restricting the connection between servers is to segment the network.
There are three basic types of network segmentation, with microsegmentation being the approach that companies can use to enforce increasingly granular policies and restrictions.
Environment segmentation
This approach separates different environments from each other. For example, in your company, the development area can be separated from the production environment. This is the first, crucial phase of any segmentation strategy, which is followed by further segmentations.
Application segmentation
This so-called “ring fencing” separates each specific, critical application from the rest of the network. The best microsegmentation solutions even enable control at the process level.
Process segmentation
The narrowest form of segmentation takes place within an application itself. Here you can create policies for managing communication between levels within the same application cluster and, for example, control traffic between web servers, application servers and database servers.
Advantages of Software-Based Segmentation
- Complete visibility in the network – “Who communicates with whom?”
- Ransomware can only spread in one segment of the network
- Automated response to attacks
What Preparations are Necessary for NW Segmentation?
- Define requirements for network segmentation
- Determination of the protection requirements of the systems to minimize the risk
- Planning of network segmentation using hardware/software-based solutions
- Implementation of network segmentation
3. Comparison of hardware- and software-based segmentation
A subsequent network segmentation, with a hardware-based firewall, requires a restructuring of the existing IT infrastructure.
This must be planned accordingly and implemented across all required systems.
In most cases, this results in a high expenditure of time and effort, which entails downtime of the services provided and, if necessary, a subsequent adjustment to the software.
A subsequent network segmentation, which is implemented with a software-based solution, can take place without interruption during ongoing operation, as the existing IT infrastructure does not have to be changed.
Thanks to the software-based approach, the corresponding communication relationships (down to the process and user level) are logged and can then be used to create the segmentation. Regardless of which network (data center, on premises, cloud) the systems are located in.
Guardicore Centra
…offers the industry’s most comprehensive and flexible solution for host-based network segmentation with the following key features:
- Broad coverage: Microsegmentation policies are implemented wherever your applications are running – in public, private, or hybrid cloud environments.
- Deep Visibility: Guardicore’s solution helps you understand the full context through application discovery and dependency mapping before you define security policies.
- Intuitive Workflow: Guardicore Centra offers a simple workflow. From mapping application dependencies to recommending and defining rules. This is how you learn to understand connections in order to then apply them optimally to data traffic.
- Granular Policies: Now you can define and enforce rules at the process level. This is how you precisely control the flow between individual application components in order to achieve the highest level of security.
- High flexibility at low costs: Guardicore’s solution is more cost-effective, effective and adaptable than traditional firewalls.